Imagine a world where your organization is constantly under siege by cyberthreats, each one a silent ninja, ready to strike at any moment. The struggle to stay afloat feels like a never-ending uphill battle. But what if there was a shield, a powerful guardian keeping your data safe and your business running smoothly? That’s precisely what Microsoft Defender for Endpoint offers – a comprehensive security solution that safeguards your digital assets with an array of advanced technologies.
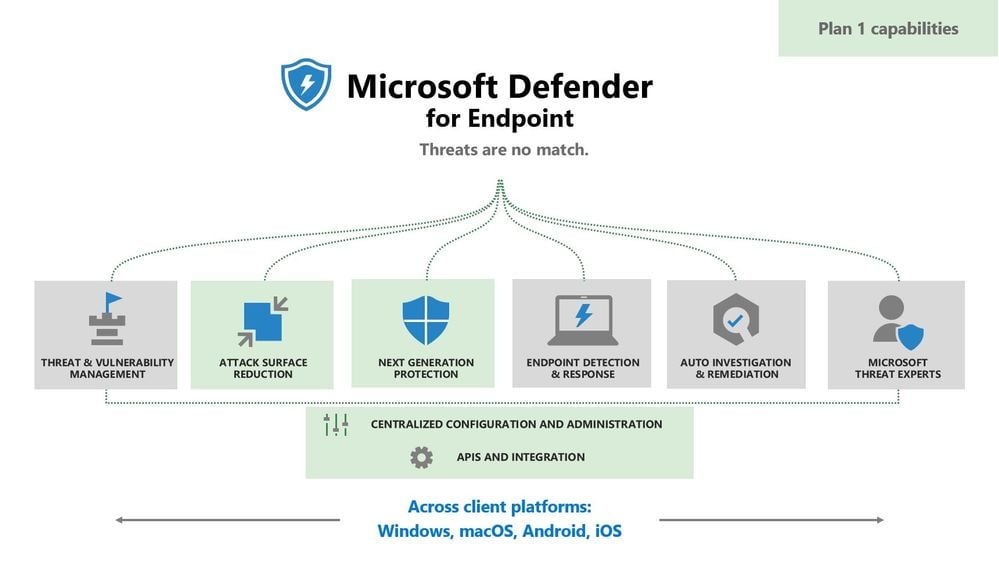
Image: thaitechnewsblog.wordpress.com
This article will serve as your comprehensive guide to Microsoft Defender for Endpoint, taking you beyond the basics and into the intricate workings of this powerful tool. We’ll unpack the features, explore its capabilities, and delve into its effectiveness in protecting your organization against today’s ever-evolving cyber threats. This is more than just a guide; it’s your roadmap to understanding how to build a robust defense strategy for your digital world.
What is Microsoft Defender for Endpoint?
Microsoft Defender for Endpoint is a cloud-based security solution that protects endpoints within your organization from sophisticated cyberattacks. It functions as a comprehensive suite encompassing endpoint detection and response (EDR), vulnerability assessment, threat intelligence, and automated remediation – all rolled into one powerful platform.
Why is Microsoft Defender for Endpoint Important?
In a world where data breaches and cyberattacks are becoming increasingly commonplace, having a comprehensive security solution is no longer optional; it’s a necessity. Microsoft Defender for Endpoint tackles this need head-on.
- Comprehensive Protection: It goes beyond traditional antivirus solutions by providing a unified platform that covers a multitude of threats, from malware and ransomware to phishing attacks and data breaches.
- Real-Time Threat Detection: It leverages advanced AI and machine learning algorithms to continuously monitor your systems for suspicious activity, enabling rapid identification and response to emerging threats.
- Automated Remediation: The system automatically takes action to isolate infected devices, quarantine malicious files, and neutralize threats before they can cause significant damage.
- Centralized Management: It streamlines security management by offering a single console for managing all your endpoint security policies, allowing you to easily monitor and respond to threats from a centralized location.
A Deeper Look: Key Features and Capabilities
Now that we’ve established the importance of Microsoft Defender for Endpoint, let’s explore the key features that make it so effective:
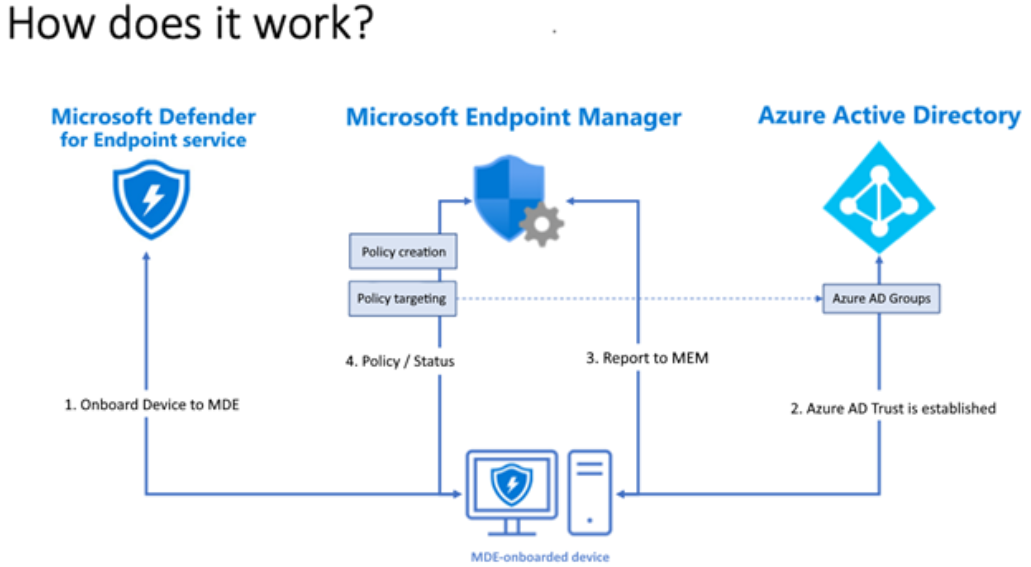
Image: hopdetrue.weebly.com
1. Endpoint Detection and Response (EDR)
EDR is the heart of Microsoft Defender for Endpoint, functioning as a 24/7 security sentinel for your endpoints. It continuously monitors for suspicious activity, provides deep insights into threats, and allows you to investigate and respond to incidents in real-time.
- Automated Threat Detection: It utilizes AI and machine learning to detect anomalous behavior and identify potential threats, even those previously unseen.
- Advanced Investigation Tools: The platform provides detailed threat information, allowing you to delve deep into attack patterns, compromised files, and affected systems. You can pinpoint the source of the attack, track its progression, and understand the tactics used by the attackers.
- Real-Time Response: EDR empowers you to take action quickly, isolating infected machines, blocking malicious websites, and even remediate vulnerabilities on the fly. This rapid response capability can significantly minimize the impact of an attack.
2. Vulnerability Assessment
Vulnerabilities are the weak points in your system’s defenses, offering hackers an easy entry point. Microsoft Defender for Endpoint proactively scans your endpoints for vulnerabilities and provides detailed information about known exploits, enabling you to patch and secure your systems before they can be compromised.
- Automated Vulnerability Scanning: The platform constantly scans your systems to identify open ports, missing patches, and outdated software, revealing potential weaknesses that hackers could exploit.
- Prioritized Remediation: It prioritizes vulnerabilities based on their severity, enabling you to focus on the most critical risks first. This ensures you’re addressing threats that pose the greatest danger to your organization.
- Detailed Reporting and Analysis: It provides detailed reports about identified vulnerabilities, including their severity, potential impact, and recommended remediation steps. This allows you to make informed decisions about resource allocation and prioritize security investments.
3. Threat Intelligence
Staying ahead of the curve in cybersecurity requires understanding the latest threats and attack tactics. Microsoft Defender for Endpoint provides access to a wealth of threat intelligence data, keeping you informed about evolving threats and enabling you to proactively defend your organization before attacks occur.
- Global Threat Intelligence: It taps into a vast network of security experts and data sources to provide insights into emerging threats, malicious actors, and attack methodologies.
- Customized Threat Alerts: The system generates alerts based on your specific environment and threat profile, ensuring you receive timely notifications about relevant threats.
- Proactive Security Posture: With real-time awareness of evolving threats, you can anticipate potential attacks, refine your security measures, and adjust your defense strategy accordingly.
4. Automated Remediation
Manual remediation of security threats can be time-consuming, prone to human error, and simply not practical in today’s fast-paced threat landscape. Microsoft Defender for Endpoint automates many critical remediation tasks, saving you valuable time and ensuring a swift and effective response to threats.
- Automated Malware Removal: It automatically detects and removes malware from infected devices, preventing further damage and containing the spread of the attack.
- Automatic Vulnerability Patching: It can automatically patch vulnerabilities on your systems, keeping your endpoints up-to-date and secure.
- Automated Threat Blocking: The platform can automatically block access to malicious websites and files, preventing users from interacting with dangerous content.
Beyond the Basics: Leveraging Advanced Capabilities
Microsoft Defender for Endpoint goes beyond just reacting to threats; it provides a proactive security posture, allowing you to anticipate and counter threats before they impact your organization.
1. Threat Hunting
Threat hunting involves proactively searching for and identifying threats within your network that haven’t been detected by traditional security measures. Microsoft Defender for Endpoint empowers you to conduct sophisticated threat hunting operations, providing tools for deep analysis and proactive threat detection.
- Advanced Query Language: It allows you to define complex queries to search for specific patterns of activity, uncovering threats that might have been missed by traditional detection methods.
- Powerful Threat Intelligence Integration: This feature enables you to leverage real-time threat intelligence data to refine your threat hunting strategies, target specific threat groups, and identify potential attack vectors.
- Full Visibility and Context: It provides detailed context for each detected threat, revealing associated indicators of compromise (IOCs), associated malware, and the specific vulnerabilities exploited by the attacker.
2. Extended Detection and Response (XDR)
XDR is a newer approach to security that goes beyond endpoint security, offering a comprehensive view of your entire IT environment, including networks, cloud resources, and email. Microsoft Defender for Endpoint seamlessly integrates with other security solutions, including Microsoft 365 Defender, providing a unified XDR experience.
- Unified Security Management: It allows you to monitor and respond to threats across your entire IT infrastructure from a single console, enabling a more holistic approach to security.
- Correlation of Security Data: It analyzes data from multiple security sources to identify potential threats, create comprehensive attack timelines, and uncover attackers’ broader motives and tactics.
- Cross-Platform Threat Hunting: It provides a single platform for threat hunting across endpoints, networks, cloud resources, and email, enabling you to detect and respond to threats that may have traversed multiple systems.
Expert Insights: Maximizing Your Defense
According to security experts at Forrester Research, “Microsoft Defender for Endpoint is a leader in the endpoint detection and response (EDR) market, providing a comprehensive security platform that encompasses advanced threat detection, investigation, and response capabilities.” To maximize its effectiveness, they recommend:
- Implement a Zero Trust Security Framework: Implement a Zero Trust security framework that assumes all users and devices are potentially untrusted, enforcing strong authentication measures and implementing least-privilege access policies.
- Combine Microsoft Defender for Endpoint with other Security Solutions: Integrate Defender for Endpoint with other security solutions, such as firewalls, intrusion detection systems, and data loss prevention tools, for a layered approach to security.
- Continuously Train and Educate Your Staff: Train your IT team on how to use Defender for Endpoint effectively and educate all employees about common cyber threats and best security practices.
Microsoft Defender For Endpoint In Depth Pdf
Conclusion: Your Path to Enhanced Security
Microsoft Defender for Endpoint is not simply a security tool; it’s a strategic investment in safeguarding your digital assets. By leveraging its advanced capabilities, threat intelligence, and automated remediation functions, you can build a robust security posture that protects your organization from the growing number of sophisticated cyber threats.
Dive deeper into this powerful tool, explore its features, and leverage its potential to empower your organization’s security.
Remember, your data is your most valuable asset. Invest in the best protection available, and build a digital world that is safe, secure, and ready to face the challenges ahead.






